QUBO AI in Cybersecurity
Quantum-Inspired Optimization
An emerging application of Quantum-inspired Optimization and Quantum Computing using the Quadratic Unconstrained Binary Optimization (QUBO) model to detect, prevent, and respond to cyber threats more efficiently than classical approaches.
🔐 What is QUBO in Cybersecurity?
QUBO is a mathematical model that maps optimization problems into binary variables with quadratic objective functions. In cybersecurity, many problems—like intrusion detection, anomaly detection, and attack path optimization—can be modeled as QUBO problems.
System Architecture
The QUBO-based IDS processes network traffic through feature analysis, generates intelligent alerts, and integrates seamlessly with Security Operations Centers for enhanced threat detection and response.
Real-time Processing
Continuous analysis of network traffic and feature anomalies for immediate threat detection.
Intelligent Alerts
QUBO optimization reduces false positives and prioritizes critical security events.
SOC Integration
Seamless integration with existing Security Operations Centers and SIEM platforms.
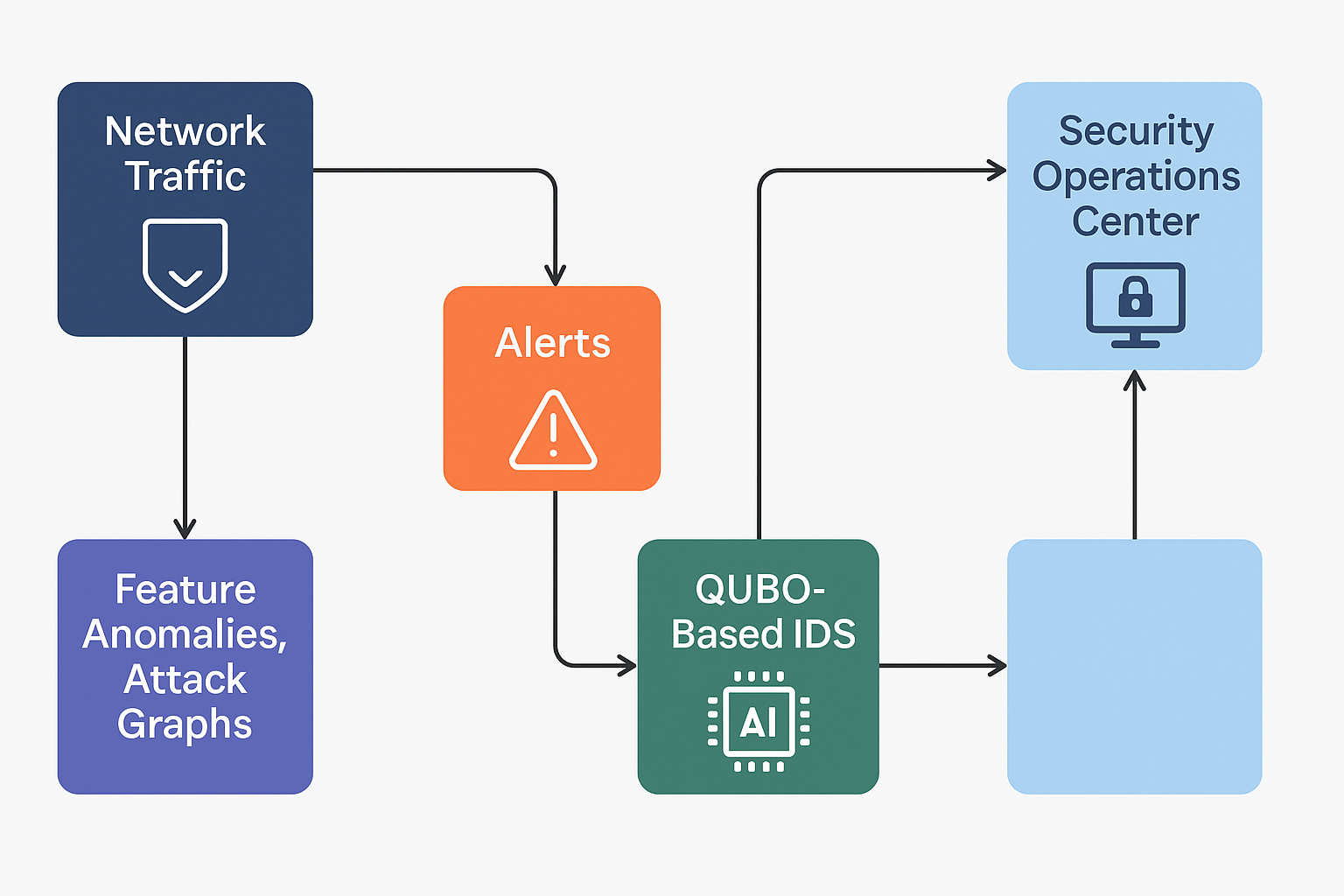
QUBO-based IDS system architecture showing the flow from network traffic analysis to Security Operations Center integration.
🧠 How AI + QUBO Helps in Cybersecurity
QUBO optimization transforms complex cybersecurity challenges into solvable mathematical problems, enabling more efficient threat detection and response.
Intrusion Detection System (IDS)
Problem: Detecting multi-step or obfuscated attacks in real-time
QUBO Solution: Models attack patterns as binary feature sets and optimizes for high-risk combinations using QUBO
Attack Graph Optimization
Problem: Huge number of potential attack paths on a network
QUBO Solution: QUBO finds the most probable or most damaging attack path
Network Hardening
Problem: Choosing minimal nodes to patch that maximize security
QUBO Solution: QUBO optimizes the patch set under budget/resource constraints
Access Control Policy Conflicts
Problem: Conflicting roles or permissions in RBAC/ABAC systems
QUBO Solution: QUBO can resolve optimal permission assignments
Cyber Deception Planning
Problem: Optimal placement of honeypots and decoys
QUBO Solution: QUBO finds configurations that mislead attackers with minimal overhead
Ransomware Response
Problem: Decide optimal files to restore or isolate
QUBO Solution: Models file recovery strategy as a constrained optimization
Phishing Email Detection
Problem: High false positives in classification
QUBO Solution: Binary encoding of email features + QUBO optimization to minimize misclassification cost
SIEM Event Prioritization
Problem: Huge log/event floods
QUBO Solution: QUBO helps prioritize which logs/alerts to triage first under analyst capacity limits
🔬 Sample QUBO Formulation: Anomaly Detection
Mathematical formulation for minimizing false negatives and false positives in detecting malicious IP behavior using QUBO optimization.
Objective Function
Minimize: Σᵢ bᵢxᵢ + Σᵢ<ⱼ wᵢⱼxᵢxⱼ
The solver finds a binary vector x representing the most probable malicious behavior profile.
xᵢ = 1 if feature i (e.g., port scan detected) is considered anomalous
Represents correlation weight between features i and j
Bias towards malicious or benign activity classification
Implementation Benefits
Optimal Feature Selection
Automatically identifies the most relevant features for threat detection while minimizing noise.
Reduced False Positives
QUBO optimization balances sensitivity and specificity to minimize both false positives and negatives.
Scalable Processing
Can be parallelized on quantum annealers or classical GPUs for high-throughput environments.
Adaptive Learning
Weights and biases can be updated dynamically based on new threat intelligence and feedback.
🔍 Feature Comparison: QUBO-Based IDS vs. Snort/Suricata
Comprehensive comparison between quantum-inspired QUBO optimization and traditional signature-based intrusion detection systems.
| Feature | QUBO-Based IDS | Snort / Suricata |
|---|---|---|
| Detection Type | Anomaly + Pattern-based via optimization | Mainly Signature-based (Snort), Hybrid with some anomaly support (Suricata) |
| Attack Path Modeling | Optimizes multi-step, stealthy attack paths using graph-based QUBO | Linear detection; no optimization over multi-stage attack graphs |
| Multi-Constraint Optimization | Handles multiple constraints (CPU, risk score, time window) in real-time | Limited; rules evaluated independently or via static thresholds |
| False Positive Reduction | Learns optimal feature sets minimizing FP/FN via binary optimization | High FP rates unless heavily tuned; static rules prone to misfire |
| Scalability | Parallelizable on GPUs/quantum annealers for large data | CPU-intensive; can slow down under high network loads |
| Adaptability to New Threats | QUBO models can adapt dynamically by re-weighting features or updating constraints | Requires manual rule updates or signatures from threat intel feeds |
| Data Handling | Works well on sparse, binary, or partially labeled datasets | Requires labeled signatures or predefined rule sets |
| Quantum-Readiness | Future-proof for quantum computing platforms | Classical-only |
| Interpretability | Moderate (QUBO outputs binary vector; explainable via weights) | High (rule-triggered alerts are human-readable) |
| Real-Time Suitability | Emerging (needs optimized solvers/hardware for live response) | Production-ready, real-time with minimal latency |
| Integration in SOCs | Prototype or experimental; needs wrapping | Widely deployed and integrated in SIEMs (e.g., Splunk, ELK) |
| Maintenance | Auto-optimizable with feedback loops | Manual updates and rule management required |
| Deployment Maturity | Experimental / early-stage | Mature, industry standard |
🔧 Best for Known Threats
Snort / Suricata excel at detecting known attack signatures
🔧 Best for Unknown Attacks
QUBO-based IDS excels at detecting novel and stealthy attacks
🔧 Hybrid Approach
Combine both for comprehensive threat detection coverage
🧪 Suggested Deployment Architecture (Hybrid):
Combine Snort/Suricata for real-time, known attack detection, and deploy QUBO-based co-processor to analyze:
- • Attack graphs
- • Feature anomalies
- • Alert prioritization
This hybrid setup can be part of a next-gen AI-powered Security Operations Center (SOC).
🧪 Tools & Frameworks
Quboscale-AI integrates with leading quantum and classical optimization frameworks for maximum flexibility and performance.
D-Wave Ocean SDK
Quantum annealing for large-scale QUBO problems
Fixstars Amplify
Quantum-inspired optimization on CPU/GPU
PyQUBO
Python library for formulating QUBO problems
AWS Braket
Hybrid quantum-classical computing platform
IBM Qiskit
Quantum computing framework with QUBO conversion
qbsolv
Classical QUBO solver for immediate deployment
💡 Novel Research/Patentable Ideas + Preparing Drafting
Cutting-edge research directions and innovative applications of QUBO optimization in cybersecurity that represent potential intellectual property opportunities. We are working on it!
Sequential QUBO IDS
QUBO-based IDS that dynamically updates based on multi-step attack patterns, learning from attack sequences to improve detection accuracy.
Quantum-Resistant QUBO IDS
Combines QUBO optimization with post-quantum cryptography to detect quantum-era threats while maintaining quantum-safe operations.
QUBO-based Access Reconciliation Engine
Resolves conflicting access permissions across systems automatically using QUBO optimization to balance security and usability constraints.
🇮🇳 Strategic Fit for India
Quboscale-AI aligns perfectly with India's cybersecurity initiatives and critical infrastructure protection goals, offering significant opportunities for deployment and innovation.
MeitY Alignment
Could align with MeitY's Cybersecurity Innovation Challenge and support India's National Cyber Security Strategy implementation.
Critical Infrastructure
Fits well in critical infrastructure protection including power grid, railways, telecom, and financial systems security.
SOC Deployment
Can be piloted in CERT-In SOCs or Smart City Security Operations Centers for real-world validation and deployment.
Ready to Transform Your Cybersecurity?
Experience the power of quantum-inspired QUBO optimization for advanced threat detection, attack path analysis, and intelligent cybersecurity decision-making.
